CVE-2023-50069
2023-12-27
Summary
WireMock with GUI versions 3.2.0.0 through 3.0.4.0 are vulnerable to stored cross-site scripting (SXSS) through the recording feature. An attacker can host a malicious payload and perform a test mapping pointing to the attacker’s file, and the result will render on the Matched page in the Body area, resulting in the execution of the payload. This occurs because the response body is not validated or sanitized.
Tested Versions
3.2.0.0 3.1.0.0 3.0.4.0
POC
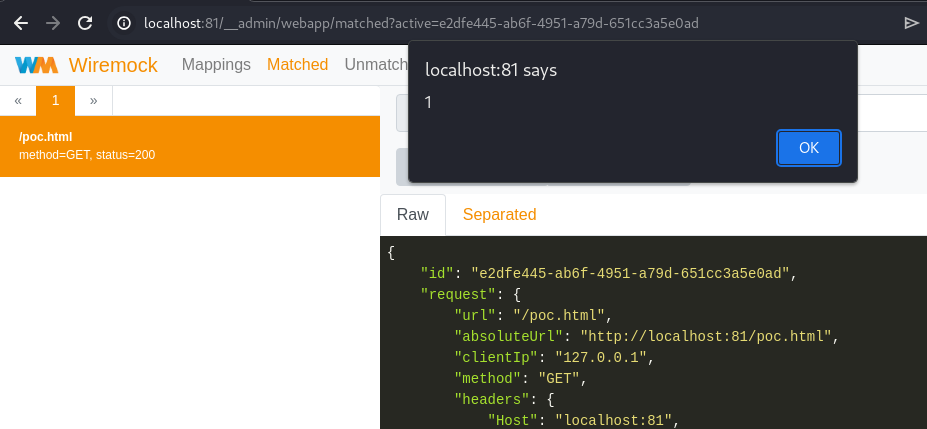
Recommendations
- Follow the offical Wiremock documentation to prevent proxying to unintended locations.
- Update to the latest release of Wiremock with GUI.
References
- [CVE-2023-50069] (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-50069)
- https://wiremock.org/docs/configuration/#preventing-proxying-to-and-recording-from-specific-target-addresses
CVSS
Attack Vector: Network Attack Complexity: Low Privileges Required: None User Interaction: Required Scope: Changed Confidentiality Impact: Low Integrity Impact: Low Availability Impact: None