2024 SANS Offensive Operation CTF - JavaScript Stage 001-003
2024-02-28
Summary
We heard you like JavaScript? So we scrambled some nice JavaScript ☕ code for you to review! Review the provided code snippet and send appropriate API request to get the flag!
JavaScript 001
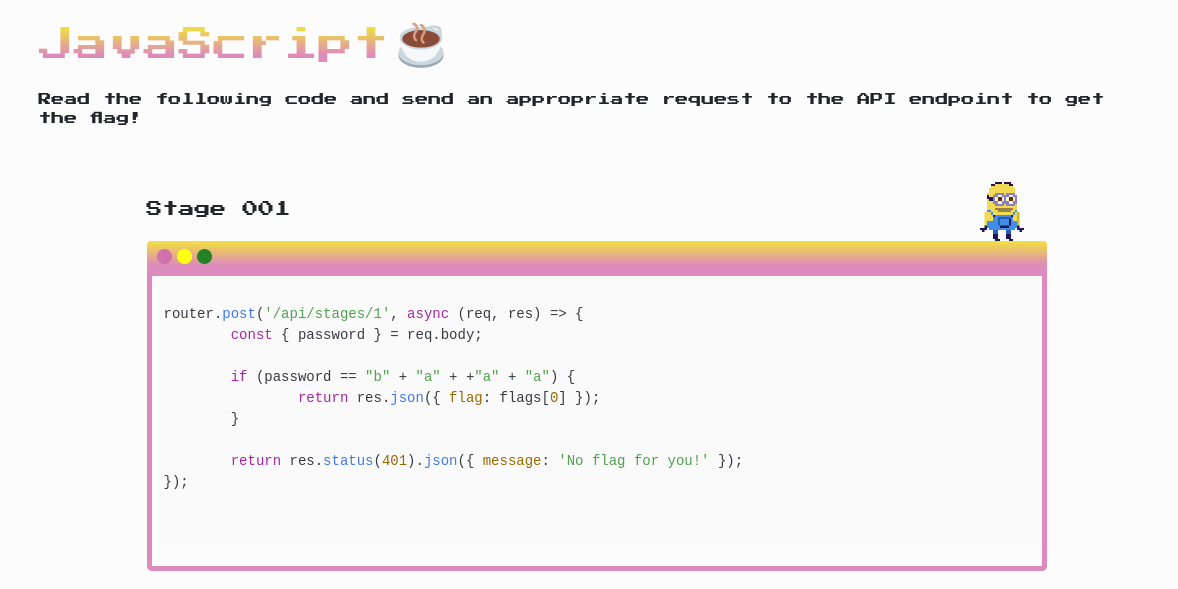
Using the provided javascript I used the browsers console to help piece together the string.
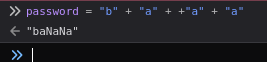
As we see in the screenshot, the value for "b" + "a" + +"a" + "a" is equals to baNaNa. This happens because the javascript is processing the space and reporting it as NaN (Not-a-Number).
Using this value, I sent a post request to the endpoint to get the flag
curl -X POST http://js.pwn.site:1995/api/stages/1 -H "Content-Type: application/json" -d '{"password":"baNaNa"}'
I received the following response:
{"flag":"flag{B-baNaNa?baNaNa!baNaNa!baNaNa!}"}%
JavaScript 002
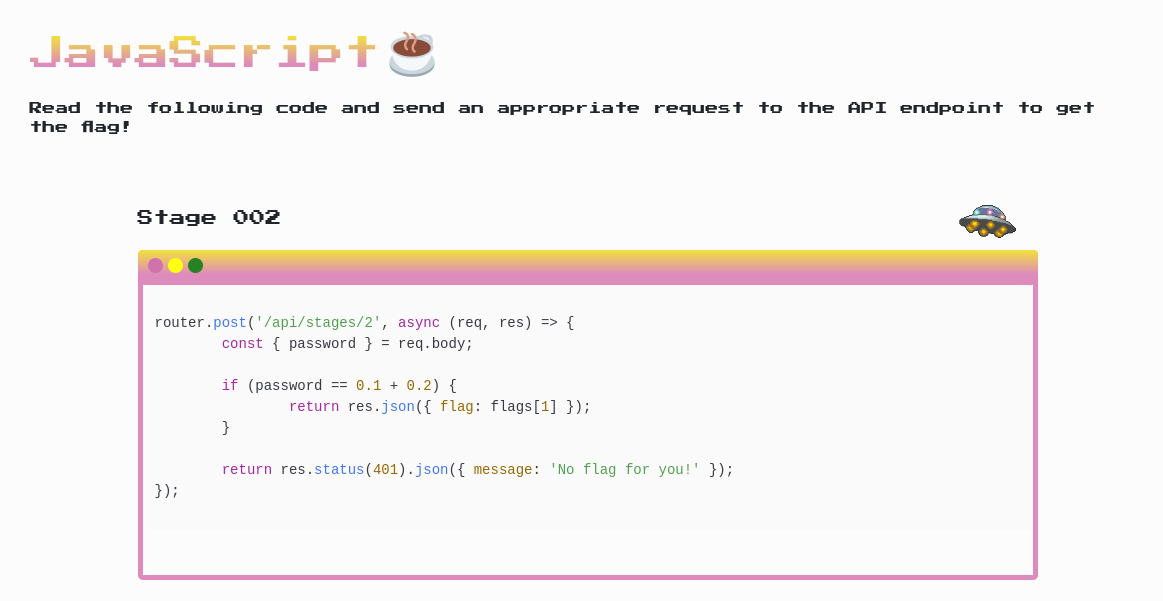
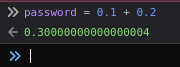
In challenge 002 we need to determine the answer for 0.1 + 0.2 as a password to the /2 endpoint. Using the same technique, I let the browser perform the operation for me giving me a value of 0.30000000000000004
Next, I again sent a POST request to the /2 endpoint.
curl -X POST http://js.pwn.site:1995/api/stages/2 -H "Content-Type: application/json" -d '{"password":"0.30000000000000004"}'
The system provided the following flag.
{"flag":"flag{IEEE-754-floating-with-you!}"}%
JavaScript 003
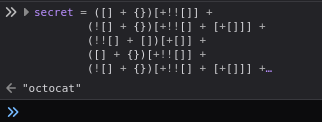
For JavaScript challenge 003, this technique utilized jsfuck to obfuscate the javascript. However, the browser will easily decode this into the intended string for us as octocat.
Again, I sent another POST request and got the flag.
curl -X POST http://js.pwn.site:1995/api/stages/3 -H "Content-Type: application/json" -d '{"password":"octocat"}'
{"flag":"flag{w31rD-j4v45cr1p7-m0m3nt!}"}%