2023 HuntressCTF - M Three Sixty Five
2023-11-01
Summary - General Info
Author: @David Carter
Welcome to our hackable M365 tenant! Can you find any juicy details, like perhaps the street address this organization is associated with?
Steps
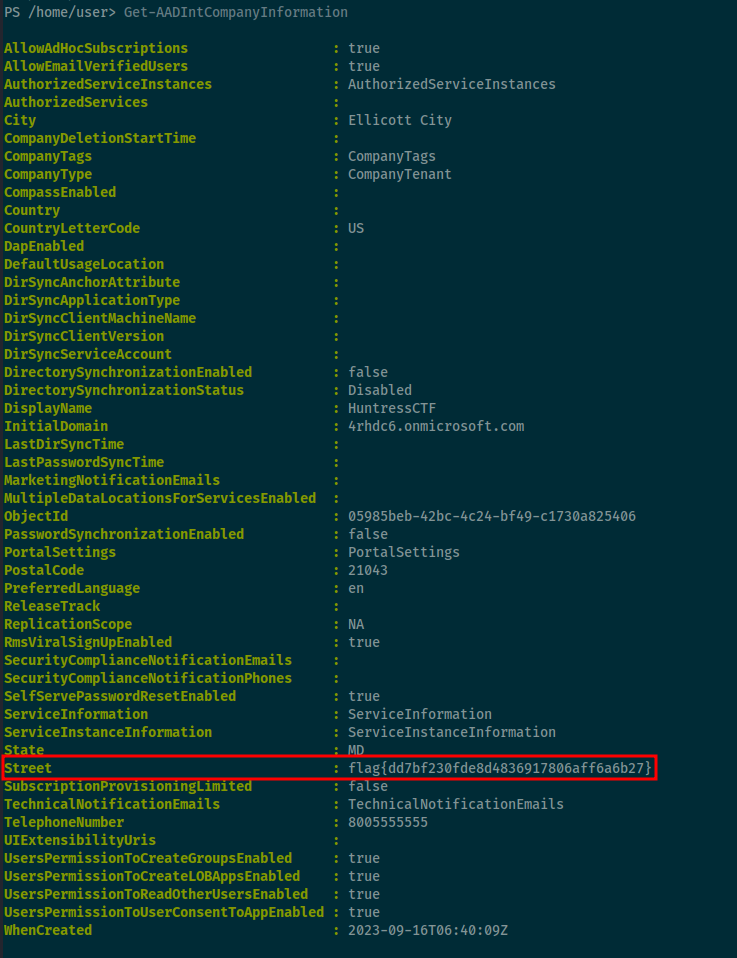
Upon authenticating to the server, I noticed the ADDInternal suite of tools was being used. I looked at the documentation for AADInternals by DrAzureAD and found a cmdlet for Get-AADIntCompanyInformation which had the flag.
Flag: flag{dd7bf230fde8d4836917806aff6a6b27}
Summary - Conditional Access
Author: @David Carter
This tenant looks to have some odd Conditional Access Policies. Can you find a weird one?
Steps
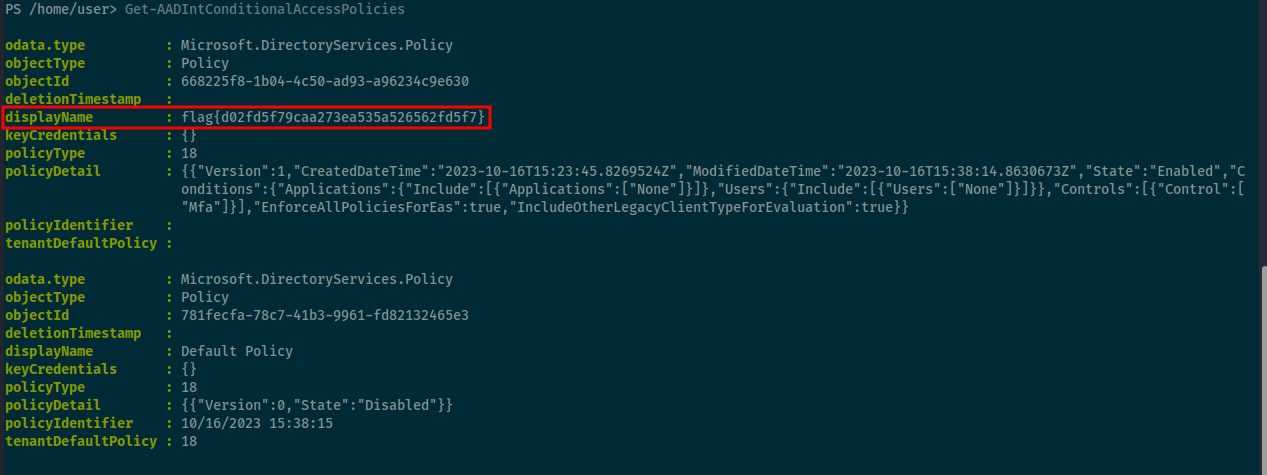
Referencing the documentation again there was a cmdlet for Get-AADIntConditionalAccessPolicies which listed our the conditional access policy and the flag was in the displayName field.
Flag flag{d02fd5f79caa273ea535a526562fd5f7}
Summary - Teams
Author: @David Carter
We observed saw some sensitive information being shared over a Microsoft Teams message! Can you track it down?
Steps
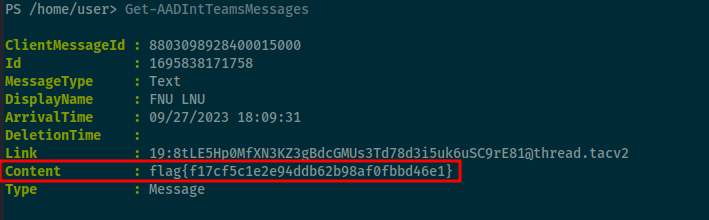
Using the Get-AADIntTeamsMessage cmdlet I found there was a flag that was sent with teams.
Flag: flag{f17cf5c1e2e94ddb62b98af0fbbd46e1}
Summary - The President
Author: @David Carter
One of the users in this environment seems to have unintentionally left some information in their account details. Can you track down The President?
Next, I used Get-AADIntUsers | select UserPrincipalName, DisplayName, Department, Title to get a quick view into the users, department and title of the User objects in this domain.
UserPrincipalName DisplayName Department Title
----------------- ----------- ---------- -----
[email protected] Lee Gu Manufacturing Director
[email protected] Alex Wilber Marketing Marketing Assistant
[email protected] FNU LNU
[email protected] CompromisedAcct
[email protected] Johanna Lorenz Engineering Senior Engineer
[email protected] Lynne Robbins Retail Planner
[email protected] Henrietta Mueller R&D Developer
[email protected] Joni Sherman Legal Paralegal
[email protected] Adele Vance Retail Retail Manager
[email protected] Diego Siciliani HR HR Manager
[email protected] Lidia Holloway Engineering Product Manager
[email protected] Nestor Wilke Operations Director
[email protected] Patti Fernandez Executive Management President
[email protected] Pradeep Gupta Finance Accountant
[email protected] Grady Archie R&D Designer
[email protected] Megan Bowen Marketing Marketing Manager
[email protected] Isaiah Langer Sales Sales Rep
[email protected] Miriam Graham Sales & Marketing Director
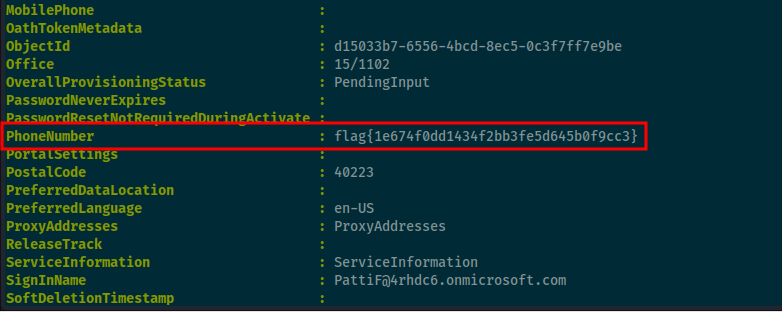
Knowing that the President is Patti Fernandez, I want to next few all details on this account. I used powersehell get-AADIntUser -UserPrincipalName "[email protected]" and found the flag listed in the PhoneNumber field.
Flag: flag{1e674f0dd1434f2bb3fe5d645b0f9cc3}